Enterprise Security with HPE Fortify
By: Richard Howe
CIO’s today are faced with many challenges. Whether it be the abundance of data from the rise of mobile and cloud computing, or their ever-changing role within the IT department, these shifting responsibilities too often end with application security falling through the cracks. Following increased budget constraints and diminishing resources, many find it difficult to scale or fund their application security programs. Only when a security threat rears its ugly head is the reaction swift, but often time consuming and all too costly to repair.
Do You Trust Your Software?
Business software today is more accessible than ever. Even legacy and in-house applications like HPE Fortify are now available on the web, in the cloud, and even on mobile devices. As a consequence, today’s applications extend far beyond the reach of most perimeter defenses, leaving the sensitive information at the core of your enterprise dangerously unprotected. Adversaries are organized, specialized, motivated, and highly skilled at exploiting vulnerabilities in software to:
- Steal data, customer identities, intellectual property, and cash
- Disrupt business operations and inflict brand damage
- Place employees, customers, and the public at risk
Exploitable Vulnerabilities Occur at the Application Layer
80% of all breaches exploit vulnerabilities at the application layer, making perimeter-based solutions too often insufficient. The vast majority of security spending goes toward blocking adversaries on the network level, focusing on the perimeter by preventing malware and viruses. These solutions can be effective for what they are designed to do, however, they are ultimately insufficient when blocking the diverse threats pitted against enterprise applications.
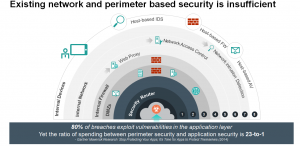
Ratio of spending for Perimeter Security and Application Security is Massively Imbalanced. Analysts have estimated a 23-to-1 ratio on network spending vs. app security.
Where Do I Start to Address Application Agile Security in My Organization?
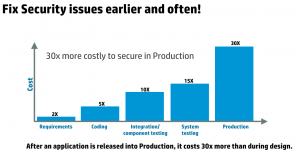
Whether your organization is utilizing a “Waterfall” or an “Agile” development methodology, security analysts recommend addressing the security vulnerability as early as possible in the project lifecycle. Study after study indicates that responding to or applying a fix to a security breach for an application in production is more costly than addressing an issue in the coding or design phase.
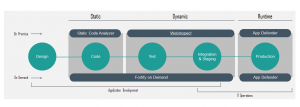
Securing Your Development Lifecycle with HPE Fortify
HPE Security Fortify offers the broadest set of agile security software products to cover the entirety of your SDLC. HPE Fortify is the ONLY Application Security that offers solutions covering SAST, DAST, IAST and RASP.
- HPE Security Fortify Static Code Analyzer, Static Application Security Testing (SAST) ––Identify the root cause of vulnerabilities during development, and prioritizes those critical issues when they are easiest and least expensive to fix. Detects 691 unique categories of vulnerabilities across 22 programming languages and spans over 835,000 individual APIs.
- HPE Security DevInspect ––Empowers developers to accelerate development by identifying and remediating security vulnerabilities in source code within the development environment in real-time, enabling them to integrate security even earlier in the SDLC.
- HPE Security WebInspect, Dynamic Application Security Testing (DAST) ––Automated dynamic testing offering that identifies security vulnerabilities and prioritizes the critical issues for root-cause analysis in running Web applications and Web services. Integrates runtime analysis to identify more vulnerability by expanding coverage of the attack surface.
- HPE Security Application Defender, Runtime Application Self-Protection (RASP) ––Identifies attacks on software vulnerabilities and other security violations in production applications and protects them from exploitation in real time.
To take advantage of the incredible agile security tools available in HPE Fortify, contact one of our ResultsPositive security experts. We’ll assess your enterprise vulnerabilities and offer custom solutions for your organization incorporating the latest HPE security technology.
Subscribe for the latest RP Blog Updates:










